Bragging Rights
Explore the latest trends, tips, and stories that make you stand out.
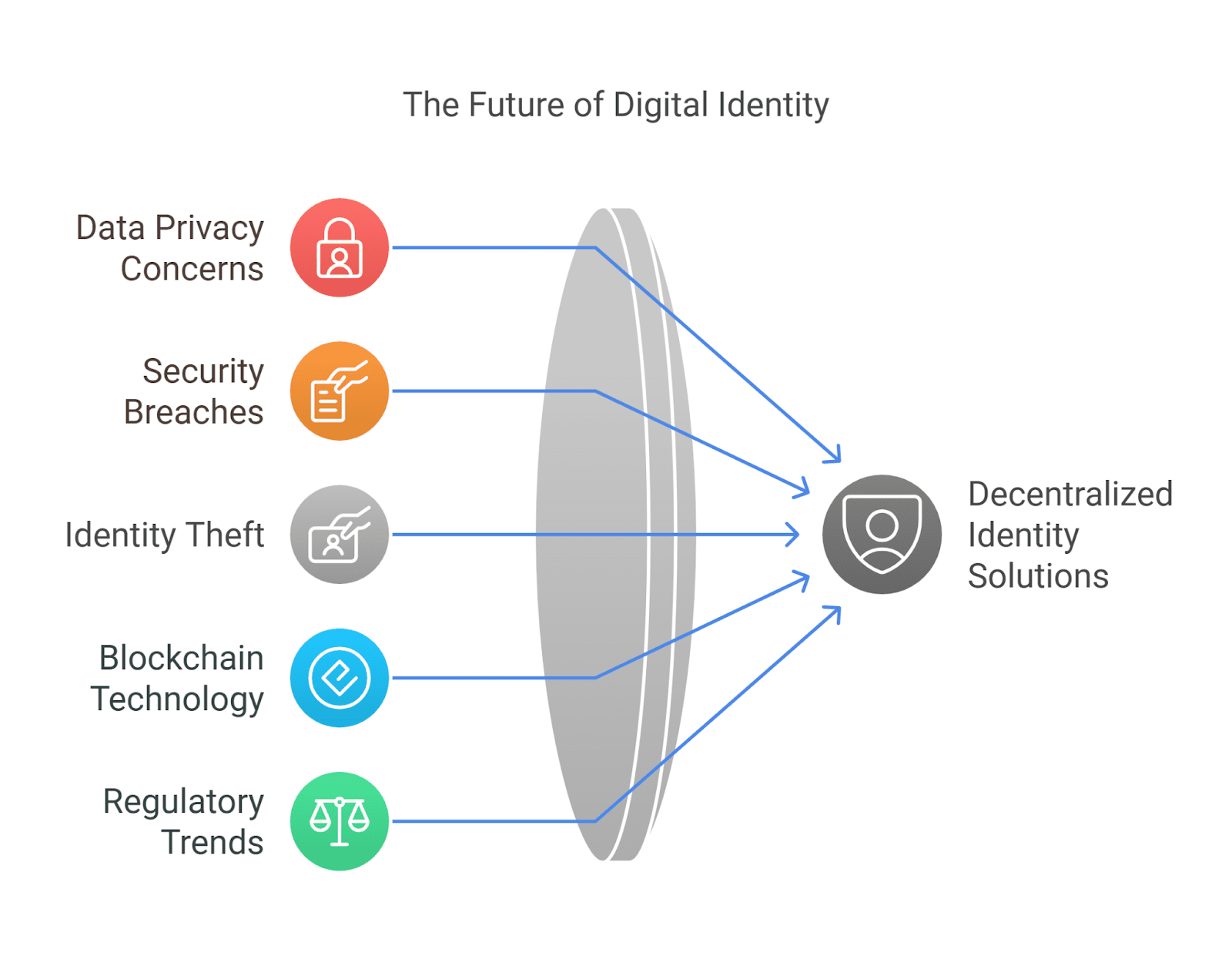
Decentralized Fortresses: The Future of Secure Platforms
Discover how decentralized fortresses are revolutionizing digital security. Explore the future of secure platforms that protect your data like never before!
Understanding Decentralization: How Fortresses Enhance Digital Security
Understanding Decentralization is crucial in today’s digital landscape, especially with threats to data privacy and security on the rise. One innovative approach to bolster security is through the use of fortresses, which serve as decentralized networks. Unlike traditional centralized systems that can be more susceptible to breaches, decentralized fortresses distribute data across multiple locations. This distribution minimizes the risks associated with a single point of failure, making it significantly more challenging for cyber attackers to compromise the entire network.
Moreover, the implementation of decentralized fortresses enhances the integrity and availability of data. When data is spread across various nodes, it not only secures information but also improves data recovery processes in the event of a cyber incident. As we navigate the complexities of modern security threats, embracing decentralization through these fortified structures can provide organizations with a more resilient framework to protect sensitive information. Adopting such strategies is essential for staying a step ahead in the face of evolving cyber threats.
Counter-Strike is a popular multiplayer first-person shooter game that has maintained a strong competitive scene since its original release. Players can choose to play as either terrorists or counter-terrorists, and the objective often revolves around completing specific missions or eliminating the opposing team. For those looking to enhance their gaming experience, check out this cryptocasino.com promo code that can offer great bonuses.
The Role of Blockchain in Creating Invulnerable Secure Platforms
The advent of blockchain technology has revolutionized the way we perceive security in various digital platforms. By utilizing a decentralized and distributed ledger system, blockchain creates an environment where data integrity is paramount. Every transaction is recorded in blocks that are then linked to one another securely; this design makes it nearly impossible for hackers to alter any information without affecting subsequent blocks. As a result, blockchain inherently promotes transparency and trust among users, paving the way for applications in sectors such as finance, healthcare, and supply chain management.
Moreover, the implementation of smart contracts on blockchain platforms further enhances security by automating and enforcing contract terms without the need for intermediaries. These self-executing contracts not only minimize the risk of fraud but also expedite transactions, making platforms more efficient overall. By integrating blockchain into their infrastructure, businesses can replace traditional, vulnerable systems with invulnerable solutions that offer enhanced security measures, thereby gaining a competitive edge in the digital landscape.
Are Decentralized Fortresses the Key to Protecting User Privacy Online?
In an era where digital privacy is constantly under siege, the concept of decentralized fortresses has emerged as a pivotal solution for protecting user data. Traditional centralized models, where sensitive information is stored on single servers, are increasingly vulnerable to breaches and hacks. By contrast, decentralized systems distribute data across multiple nodes, making it significantly more challenging for malicious actors to target and compromise user information. This shift from a centralized to a decentralized approach not only enhances security but also ensures that users maintain greater control over their personal data.
Moreover, integrating decentralized fortresses into existing digital platforms can address concerns surrounding surveillance and data ownership. These fortresses empower users by enabling them to interact and share information without relying on intermediary entities that may exploit their data. As awareness grows regarding the importance of online privacy, adopting decentralized technologies can usher in a new era of secure, user-centric digital experiences. Indeed, the question remains: are decentralized fortresses the key to ensuring lasting privacy protection, or can we expect traditional systems to adapt and evolve in order to safeguard users against the ever-present threats of the internet?